A paradigm-shift to secure code and seamless integration in the software development lifecycle.
Software plays a critical role in handling sensitive information on devices like laptops, smartphones, and cars. Modern software applications are almost never built from scratch but reuse a significant amount of code that has been built by third parties. These code artefacts, in the form of externally developed libraries, packages and frameworks form the core of the so-called software supply chain.
However, security remains a significant concern. Unauthorized disclosure or corruption of data may result in financial damage, privacy violations, and loss of human lives. The challenge is compounded by complex software systems and reliance on third-party code. To address this, we must prioritize code security and seamlessly integrate it into the software development lifecycle.
This project aims to enhance security by analysing and fortifying the supply chain of software applications and third-party code, offering novel security models, algorithms, and tools for developers to identify, visualize, prioritize, and mitigate security risks.
Long term impact
ShiftLeft will contribute to a new paradigm shift for securing software supply chains (SSC). The project will address the strategic goal to enhance the security of computer systems, as outlined in Sweden’s ‘national cybersecurity strategy’ and the EU’s Cyber Resilience Act.
Modern software applications are rarely built from scratch; they often reuse code developed by third parties. While cost and timeliness are important benefits, software supply chains and the artefacts are increasingly vulnerable to cybersecurity attacks. Just a few lines of code can introduce security vulnerabilities across multiple software systems.
The SHIFTLEFT project contributes to securing the software supply chain without disrupting the software development practices. The project will deliver a principled, comprehensive, and practical code-centric solution to securing the software supply chain.
The goal is to contribute to a new paradigm shift for securing the software supply chain. The proposed paradigm is based on a declarative code-centric platform supporting continuous security analysis at scale by means of novel abstractions.
The team of PIs consists of four renowned researchers with complementary skills:
Musard Balliu is an associate professor at the division of theoretical computer science at KTH Royal Institute of Technology. He leads the LangSec (Language-Based Security) group conducting research at the intersection of computer security, programming languages, formal methods and software engineering.
Alexandre Bartel is a professor in software engineering and computer security at Umeå University.
Christoph Reichenbach is an associate professor at Lund University and researcher in software technology, specifically programmer productivity tools, program analysis, and domain-specific languages.
David Sands is a professor in Computer Science at Chalmers University of Technology. His main research areas are Programming Languages, Computer Security, and their combination. He leads the ProSec research group (Programming Language Based Methods for Security).
Rebekka Wohlrab is an assistant professor in Software Engineering at Chalmers University of Technology. She is also an adjunct faculty member at Carnegie Mellon University.
Scientific presentation
Background
There are fundamental and practical gaps between software development practices, the inadequacy of standard security solutions, and the solutions proposed by the research community, spanning the fields of computer security, programming languages, software engineering, and formal methods. Unfortunately, while formal methods are costly to apply at scale, programming languages require new security abstractions to accommodate seamless integration into the software development lifecycle. Current code-centric approaches are a useful starting point, however they suffer from the above-mentioned drawbacks. Further, practices in software technology incorporate incremental development through continuous integration, thus we need novel approaches to security that fit this model.
Purpose
This project aims to enhance security by analysing and fortifying the supply chain of software applications and third-party code, offering novel security models, algorithms, and tools for developers to identify, visualize, prioritize, and mitigate security risks.
Methods
The project focuses on a code-centric software development model to secure the software supply chain through a new paradigm shift that enables building secure applications with a minimal change in the development practices while providing effective feedback to the developer.
Key insights
The key insights are centred around a unified platform for continuous security analysis that exposes security abstractions to the developer, including language support for specifying security policies against different classes of vulnerabilities. This platform would serve as a database of facts that the developer can query declaratively to evaluate the risks of reusing code from the SSC into their software application.
The key innovations of SHIFTLEFT are:
- A foundational framework for SSC security
- Novel abstractions to combine static and dynamic techniques, incorporating a range of vulnerability-specific analysis
- Human-in-the-loop feedback and AI-driven prioritization metrics enabling effective practical use.
The research objectives of SHIFTLEFT can be summarized as follows:
- Develop the security foundations of the SSC via an expressive security model and a semantic policy framework that account for malicious components affecting integrity and confidentiality properties.
- Build a scalable and integrated security analysis platform by novel combinations of static and dynamic analysis to support query-based identification of vulnerabilities via novel abstractions.
- Develop the first open-source security dashboard that integrates human-in-the-loop feedback into the software development lifecycle, in line with the continuous integration pipeline.
- Demonstrate feasibility and usability via largescale evaluation and validation on real-world SSCs.
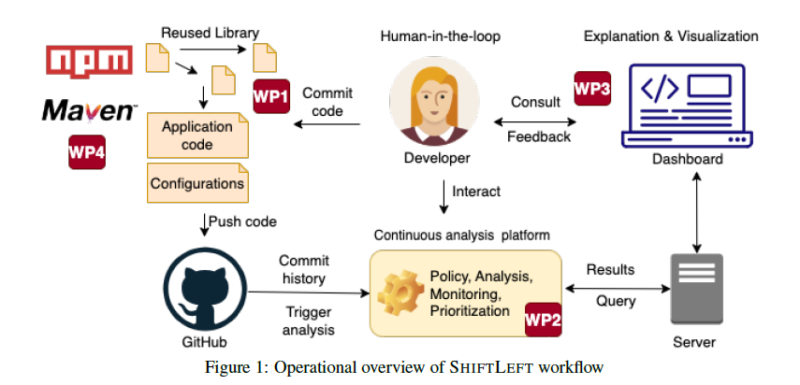
SHIFTLEFT will deliver a principled, comprehensive, and practical code-centric solution to securing the software supply chain (SSC). It is organized in four work packages (WPs) targeting each of the research objectives described above.
- WP1 develops the software supply chain security foundations and proposes a security framework to express security policies.
- WP2 focuses on an analysis platform for enforcing the policies from WP1.
- WP3 outlines the dashboard enhanced with human-in-the-loop and AI techniques to monitor and enforce policies from WP1 by techniques from WP2.
- WP4 outlines the evaluation and validation plan for the project.
Figure 1 presents an operational view of SHIFTLEFT’s contributions with the new paradigm shift, including the main focus of each WP.