DYNamic Attack detection and mitigation for seCure AutONomy. Protect autonomous systems from cyber-attacks targeting control systems.
Cyber-attacks targeting control systems, found in autonomous systems, are a relatively recent phenomenon. Unfortunately, such attacks can have a devastating impact and can harm both humans and the environment.
In DYNACON four leading research groups in cyber-physical security (control systems, real-time systems, communication and network security) at KTH, Lund University and Linköping University join forces to address the challenges of cyber-attacks in autonomous systems. The group will tackle issues such as false data injection attacks and attacks against time synchronization. The idea is to use trusted embedded devices as well as cryptographic authentication when necessary. Also, they will look into how detection and observer schemes can be developed to detect and mitigate attacks both in the local and the supervisory control.
Long term impact
The project will provide insights into methods to protect autonomous systems from cyber-attacks. The results and the insights will benefit the Swedish industry and society as a whole, as automation is increasingly critical for Swedish industry. The project group also plans to open source the code developed in the project to make it available to other researchers.
This project aims to develop theory and rigorous tools for defence against cyber-attacks on dynamical physical systems with time-critical controllers. They will specifically look at systems with a high degree of autonomy, such as drones. However, the results will be relevant in general to any multi-agent system with limited computational resources.
False data injection attacks aim to remain stealthy while allowing the injection of malicious commands into a control loop. Examples are zero-dynamics attacks that exploit non-visible actuation commands in sensor readings, making them undetectable even with secured sensors. Covert attacks are when the attacker has extensive model knowledge and control over inputs and outputs. Resilient estimators and intermittent Message Authentication Codes (MACs) are proposed defence mechanisms against some false data injection attacks.
DYNACON will extend these concepts to address the challenges in the considered distributed system architecture, including covert attacks and manipulation of the Controller and Local Observer.
The project comprises a group of senior researchers within cyber-security, real-time systems, control theory, and machine learning to ensure trustworthy control systems.
The PIs, along with related projects and WASP PhD students, form a strong foundation for the cyber-physical security WASP HOTspot.
Scientific presentation
Background
Control systems are at the heart of many indispensable societal functions, from energy distribution to pacemakers. Although we rely on these systems, cyber-physical controllers have been increasingly targeted by cyber-attacks, from critical infrastructures such as power grids to commercial IoT devices.
Purpose
This project aims to develop rigorous tools for defence against cyber-attacks on dynamical physical systems with time-critical controllers. The project specifically targets systems with a high degree of autonomy, such as drones. However, the results will be relevant to any multi-agent system with limited computational resources.
Methods and approach
Figure 1 illustrates the key components of control architectures the project group considers. The architecture includes the embedded Controller and Local State Observer, which are co-located with the physical Plant and communicate using the channels and. Each plant (agent), such as a drone, has a high degree of autonomy. The outer communication links , which can be realized using wireless technologies such as WiFi, 5G, Bluetooth, involve edge computing devices hosting Anomaly Detector(s) and Global State Observer(s). The edge layer enables agent coordination and identification, as well as coordinated anomaly detection and defense.
The project group focuses on two general types of cyber-attacks against the agents: (i) the attacker has infiltrated the embedded system and can influence the task execution; and (ii) the attacker can inject or modify packets (data) in the communication links.
The overall research challenge is the design of security mechanisms to mitigate and detect these types of attacks, subject to given resource constraints and control specifications.
More specifically, this NEST will focus on the following research challenges:
(A) False-data injection attacks and authenticated resilient state observers
(B) Timing attacks and switched trusted execution environments
(C) Identity spoofing and robust remote agent identification
(D) Situational awareness and human-in-the-loop AI for intrusion detection
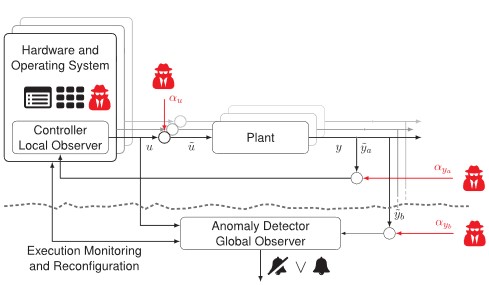
Figure 1: Illustration of Dynacon System Architecture and some attack vectors. Several local, autonomous control systems are monitored through a centralized control center.
Challenge A – False-data injection: False-Data Injection attacks can cause physical damage and loss of situational awareness. Due to time constraints and limited computational resources, cryptographic authentication for every data packet is impractical. Instead, the project proposes an adaptive defense framework that combines resilient state observers with partial cryptographic authentication.
Challenge B – Timing: Timing plays a critical role in complex control systems. A glitch in the image pipeline caused the loss of a single image, resulting in inaccurate timestamps for subsequent images. If the attacker causes deadline misses in a classical control system, the consequences can be significant. However, deadline misses in control systems that are fed by sensor pipelines are even harder to deal with. The focus here is on defending the Controller and Local Observer against misalignments in multi-sensor pipelines and artificially introduced computational delays.
Challenge C – Remote agent identification: Similar to cars, drones require digital ”number plates” for law enforcement purposes. Current regulations mandate the broadcasting of drone IDs using WiFi or Bluetooth, which can easily be spoofed through False-Data Injection attacks. This method of identification lacks security considerations. To address this, a cryptographic drone ID should be developed.
Challenge D – Situational awareness: Real-time situational awareness based on a multitude of noisy alerts from Anomaly Detectors poses a significant challenge in security monitoring. These detectors address challenges such as FDI and spoofing. The presence of a high number of false alerts leads to alarm fatigue and delays in detection. To address this, the project advocate for treating Machine Learning (ML)-enabled intrusion detection and incident response as a Human-in- the-Loop (HitL) Artificial Intelligence (AI) system. In this system, ML should be aware of the capabilities of human security analysts and have knowledge of an abstract representation of the observed system. ML should learn to effectively leverage the expertise of human analysts and control system inputs. To achieve this, we propose developing a novel framework cast as an active learning problem in a Dynamic Bayesian Network (DBN). This framework tackles fundamental issues related to learning and the computational complexity of optimal policies.
DYNACON aims at developing detection and mitigation strategies to defend from cyber-attacks on control systems. This ambitious goal is partitioned into the following scientific goals:
- SG1 Vulnerability and Impact Analysis,
- SG2 Coordinated Attack Detection,
- SG3 Moving Target Defence,
- SG4 Validation in Real-world Testbeds.


